The Need
As physical and digital infrastructures converge, organizations face growing threats to both assets and personnel. A Security Surveillance Operations Center (SOC) provides centralized monitoring, incident response, and situational awareness across facilities. Without integrated surveillance, businesses risk delayed reactions to intrusions, theft, vandalism, and safety breaches. Modern SOCs go beyond passive camera feeds—they integrate video analytics, access control, alarms, and environmental sensors into a unified platform. In system architecture, a surveillance SOC ensures real-time visibility, coordinated response, and compliance with safety regulations. Mubadara’s consulting helps design and implement SOCs that protect people, property, and operations with precision and scalability.
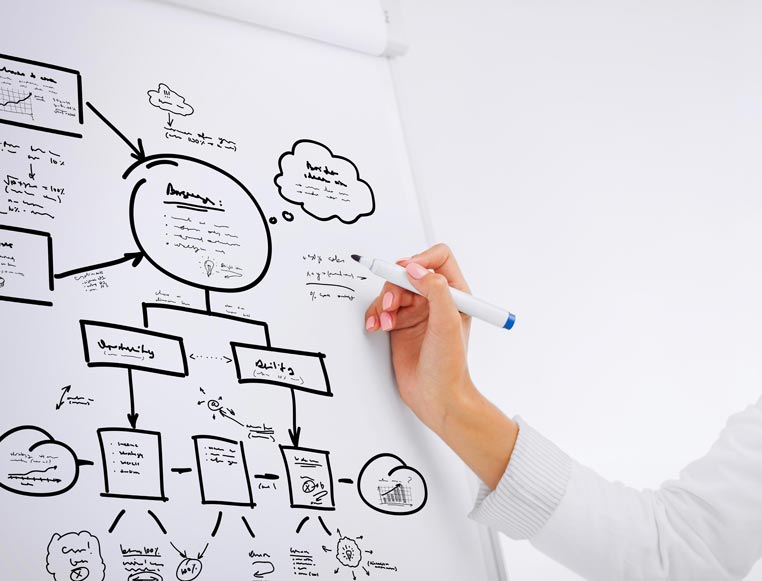

How it Works
We begin by assessing your physical security landscape, including camera coverage, access points, and existing monitoring systems. Our team designs a centralized SOC architecture that integrates CCTV, access control, intrusion detection, and environmental sensors into a unified dashboard. Video feeds are analyzed using AI-powered analytics for motion detection, facial recognition, and behavior tracking. Alerts are configured for unauthorized access, perimeter breaches, and environmental anomalies. The SOC is staffed or automated to respond to incidents in real time, with escalation protocols and reporting tools. Integration with IT systems ensures seamless coordination between physical and digital security. The result is a proactive, intelligent security hub that enhances safety and operational control.
Video Surveillance & Analytics
We deploy high-definition CCTV systems with smart analytics to monitor critical zones. AI-powered features like facial recognition, license plate reading, and motion detection enhance situational awareness. Feeds are centralized in the SOC for real-time monitoring and historical review. We also configure alerts for unusual activity and integrate with access control systems. This component ensures visibility, deterrence, and rapid response to physical threats.


Access Control Integration
We integrate access control systems—biometric scanners, RFID readers, and smart locks—into the SOC platform. This allows centralized monitoring of entry/exit points and real-time validation of personnel access. Role-based permissions and visitor management are enforced. Alerts are triggered for unauthorized access attempts or policy violations. Historical logs support audits and investigations. This component strengthens perimeter security and internal access governance.
Intrusion Detection & Alarm Systems
We implement sensors and alarm systems to detect unauthorized entry, tampering, or forced access. These include motion detectors, glass break sensors, and door contact alarms. Alerts are routed to the SOC for immediate action. Integration with video feeds and access logs enables rapid verification and response. Automated protocols can trigger lockdowns or notify emergency services. This component enhances threat detection and containment.


Environmental Monitoring & Safety Controls
We integrate sensors for temperature, smoke, gas leaks, and water intrusion to protect infrastructure and personnel. Alerts are configured for abnormal readings, and automated responses can activate ventilation, fire suppression, or evacuation protocols. Data is logged and visualized in the SOC dashboard. This component ensures environmental safety and supports compliance with health and safety regulations.
Unified Command Dashboard
We design a centralized dashboard that consolidates video feeds, sensor data, access logs, and alerts into a single interface. Operators can monitor, investigate, and respond to incidents efficiently. Dashboards are customizable based on roles and zones. Integration with mobile apps and remote access tools allows off-site monitoring. This component improves situational awareness and operational control.

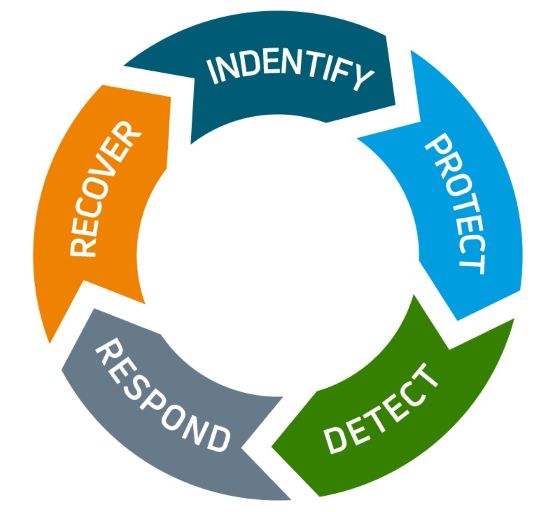
Incident Response & Escalation Protocols
We develop structured workflows for responding to security incidents. This includes alert classification, escalation paths, and communication protocols. SOC operators are trained to follow predefined playbooks for various scenarios. Integration with emergency services and internal teams ensures coordinated response. Incident logs are maintained for analysis and reporting. This component ensures fast, organized, and effective incident management.
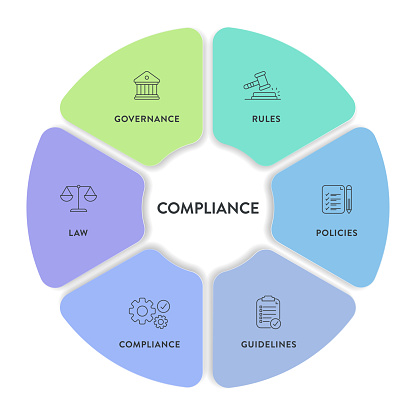
Audit Trails & Compliance Reporting
We configure systems to maintain detailed logs of access events, video footage, sensor alerts, and operator actions. These logs support internal audits, regulatory compliance, and forensic investigations. Reporting tools generate summaries for management and authorities. Our solutions align with standards like ISO 27001, NCA ECC, and local safety regulations. This component ensures accountability and legal readiness.
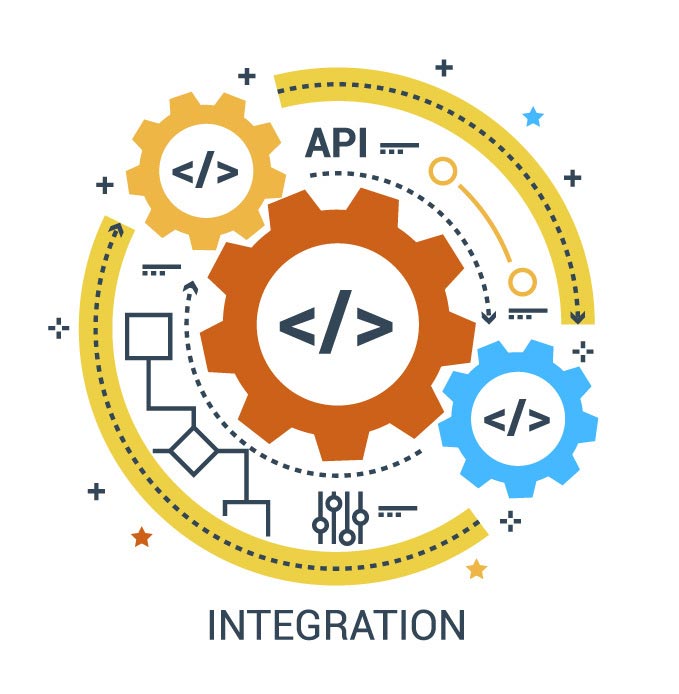
Integration with IT & Facility Systems
We enable seamless integration between the SOC and IT infrastructure, including network monitoring, cybersecurity platforms, and building management systems. This unified approach allows coordinated response to both physical and digital threats. For example, a physical breach can trigger network lockdowns or alert IT teams. This component supports holistic security and operational efficiency.


