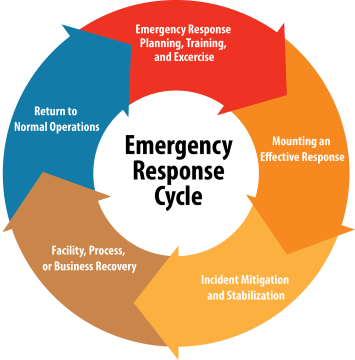
The Need
While digital threats often dominate security discussions, physical security is equally critical in protecting system architecture. Unauthorized physical access to servers, network devices, or data centers can lead to data breaches, hardware tampering, and operational disruption. As systems become more distributed—with edge computing, remote offices, and hybrid environments—the risk of physical compromise increases. Regulatory standards like ISO 27001 and NCA ECC also mandate physical safeguards. Without proper controls, even the most secure software can be bypassed through physical intrusion. Mubadara’s consulting ensures that physical security is integrated into your system architecture, protecting infrastructure, data, and personnel from real-world threats.

How it Works
Our physical security consulting begins with a site-level risk assessment, evaluating access points, surveillance coverage, and environmental controls. We analyze how physical infrastructure—servers, switches, storage units—is protected within your system architecture. Based on this, we design layered security measures including access control systems, biometric authentication, surveillance, and environmental monitoring. We also help implement policies for visitor management, equipment handling, and emergency response. Integration with digital systems ensures centralized monitoring and alerting. Our approach ensures that physical security complements your cybersecurity strategy, creating a unified defense across all layers of your architecture.
Access Control Systems
We implement physical access controls such as keycard systems, biometric scanners, and PIN-based entry to restrict access to sensitive areas. These systems are integrated with identity management platforms for centralized control. Access logs are maintained for audit and compliance. Multi-layered access zones ensure that only authorized personnel reach critical infrastructure. We also help define access policies based on roles and responsibilities. This minimizes insider threats and unauthorized entry.


Surveillance & Monitoring
We design and deploy CCTV systems with real-time monitoring and recording capabilities. Cameras are strategically placed to cover entry points, server rooms, and high-risk zones. Integration with analytics tools enables motion detection, facial recognition, and anomaly alerts. Surveillance data is securely stored and accessible for audits. We also help set retention policies and access controls for recorded footage. This ensures visibility, deterrence, and evidence in case of incidents.
Environmental Controls
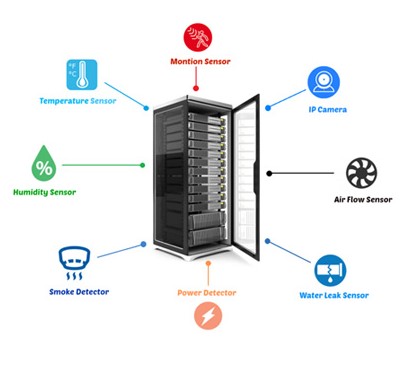
Protecting hardware from environmental hazards is essential. We implement temperature, humidity, smoke, and water leak sensors to monitor conditions in server rooms and data centers. Automated alerts and shutdown protocols prevent damage from overheating or flooding. We also advise on fire suppression systems, backup power solutions, and HVAC configurations. These controls ensure optimal operating conditions and reduce the risk of hardware failure. Regular maintenance and testing are part of our strategy.

Visitor Management & Policy Enforcement
We help establish procedures for managing visitors, contractors, and third-party access. This includes registration systems, temporary access badges, and escort policies. Visitor logs are maintained for compliance and incident tracking. We also develop physical security policies covering equipment handling, access violations, and emergency protocols. Training and awareness programs ensure staff understand and follow these policies. This creates a culture of accountability and vigilance.
Perimeter Security & Intrusion Detection
Securing the perimeter is the first line of defense. We design fencing, gates, and barriers to control physical access to facilities. Intrusion detection systems (IDS) such as motion sensors and alarms are deployed to detect unauthorized entry. These systems are integrated with surveillance and access control for coordinated response. We also help define response protocols for breaches and suspicious activity. Perimeter security ensures early threat detection and rapid containment.


Secure Equipment Placement & Cabling
We advise on secure placement of servers, switches, and network devices to prevent tampering and unauthorized access. Equipment is housed in locked racks or enclosures with restricted access. Cabling is routed through secure conduits and labeled for easy identification. We also help implement tamper-evident seals and physical port controls. This protects infrastructure from sabotage, theft, and accidental damage. Proper layout enhances both security and maintenance efficiency.
Redundancy & Emergency Preparedness
We design physical redundancy for critical systems, including backup power (UPS/generators), redundant cooling, and alternate access routes. Emergency preparedness plans cover fire, flood, and power outage scenarios. We help conduct drills and simulations to test response readiness. Emergency kits, signage, and evacuation procedures are also part of our planning. These measures ensure business continuity even during physical disruptions. The goal is to minimize downtime and protect personnel and assets.