The Need
Modern system architectures are increasingly complex, distributed, and exposed to evolving cyber threats. As businesses adopt cloud platforms, mobile access, and interconnected services, the risk of data breaches, unauthorized access, and system compromise grows significantly. Information security is no longer a standalone function—it must be embedded into the architecture itself. Without proper security integration, vulnerabilities can exist at every layer, from network protocols to application interfaces. Regulatory compliance, customer trust, and business continuity all depend on secure design. Mubadara’s consulting ensures that security is built into the foundation of your systems, not added as an afterthought. This proactive approach protects your assets, supports scalability, and enables secure innovation.

How It Works
Our approach begins with a security-focused assessment of your existing system architecture, identifying gaps in design, access control, data flow, and threat exposure. We analyze each layer—from infrastructure and middleware to applications and endpoints—to understand how security is currently implemented. Based on this, we design a security architecture that aligns with your business goals and compliance requirements. This includes integrating encryption, identity management, secure APIs, and network segmentation. We also help implement monitoring tools, incident response protocols, and governance frameworks. Our team ensures that security measures are scalable, adaptable, and embedded into every component of your system. The result is a resilient architecture that supports secure operations and future growth.
Security Architecture Design
We develop a layered security architecture that embeds protection into every part of your system—from infrastructure to applications. This includes designing secure zones, implementing firewalls, and defining trust boundaries. We ensure that security controls are aligned with business processes and technical requirements. Our architecture supports scalability, redundancy, and resilience against evolving threats. We also incorporate defense-in-depth strategies to minimize single points of failure. The design is documented for governance and future audits. Our goal is to build a secure foundation that supports innovation without compromising safety.


Identity & Access Management (IAM)
IAM is critical for controlling who can access what within your systems. We implement centralized identity platforms that manage user authentication, authorization, and lifecycle. Role-based access control (RBAC), multi-factor authentication (MFA), and single sign-on (SSO) are integrated to enhance security and user experience. We also help enforce least privilege policies and monitor access patterns for anomalies. IAM solutions are designed to scale across cloud, on-premises, and hybrid environments. This ensures consistent access control across all platforms. Our approach reduces insider threats and strengthens compliance posture.
Data Protection & Encryption
Protecting sensitive data is a top priority. We implement encryption for data at rest and in transit using industry-standard protocols. Our consulting includes secure key management, data classification, and tokenization strategies. We help you identify critical data assets and apply appropriate protection measures. Backup encryption and secure storage solutions are also part of the plan. We ensure compliance with data protection regulations like GDPR and NCA ECC. Our goal is to prevent unauthorized access, data leakage, and ensure data integrity across your systems.

Secure API & Integration Controls
APIs are essential for system interoperability but can be vulnerable if not secured properly. We assess your API landscape and implement controls such as authentication, authorization, rate limiting, and input validation. We also help you adopt secure coding practices and API gateways to manage traffic and enforce policies. Our solutions prevent injection attacks, data exposure, and unauthorized access. We ensure that third-party integrations follow your security standards. This protects your system from external threats while maintaining seamless functionality.
Network Segmentation & Perimeter Security
We design segmented network architectures that isolate critical assets and limit lateral movement during breaches. This includes implementing VLANs, DMZs, and micro-segmentation strategies. Firewalls, intrusion detection/prevention systems (IDS/IPS), and access control lists are configured to enforce perimeter defenses. We also help define network zones based on trust levels and business functions. Monitoring tools are deployed to detect suspicious activity across segments. This layered approach enhances visibility and containment. It ensures that even if one part of the network is compromised, the rest remains protected.


Security Monitoring & Incident Response
Real-time monitoring is essential for detecting and responding to threats. We deploy SIEM (Security Information and Event Management) systems to collect and analyze logs from across your infrastructure. Our incident response plans include predefined workflows for containment, investigation, and recovery. We also conduct tabletop exercises and simulations to test readiness. Alerts and dashboards provide visibility into system health and threat activity. Our team helps you build a responsive security operations center (SOC). The goal is to minimize impact and restore operations quickly during incidents.
Compliance & Governance Frameworks
We help you align your system architecture with regulatory standards such as ISO 27001, NCA ECC, and GDPR. This includes developing security policies, procedures, and documentation for audits. We also assist in setting up governance structures that define roles, responsibilities, and escalation paths. Regular reviews and gap assessments ensure ongoing compliance. Our consulting supports risk management, accountability, and transparency. By embedding governance into your architecture, you reduce legal exposure and build stakeholder trust.
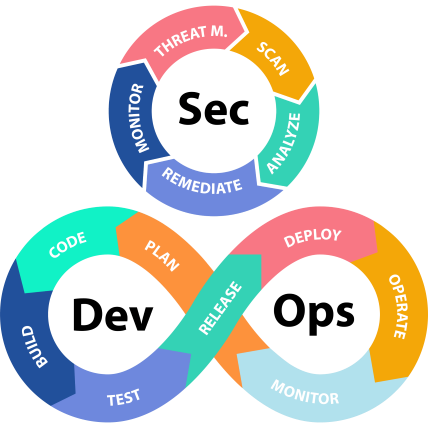
Secure Development & DevSecOps
Security must be part of the development lifecycle. We integrate DevSecOps practices that embed security checks into CI/CD pipelines. This includes automated code scanning, dependency management, and vulnerability assessments. Developers are trained in secure coding standards and threat modeling. We also help implement version control, rollback mechanisms, and secure deployment workflows. Our approach ensures that security is continuous—not just a final step. This reduces risk, speeds up delivery, and ensures that applications are secure from the start.


